Zero Trust Security
Comprehensive support for implementing the optimal security model for the modern cloud-native era with widespread remote work and digital transformation
- Home
- Products & Services
- Solution Products
- Zero Trust Security
- Zero Trust Security
- Cato Cloud
What is zero trust security
Zero trust security is a new approach to cybersecurity that protects an organization's information assets from threats by treating any access as untrusted and validating it, abandoning the traditional concept of a perimeter between the inside and outside of a network.
Features
-
01 Zero Trust Network Access (ZTNA)

ZTNA is a new model of network security based on zero-trust strategies. Rather than controlling access based on network perimeters, the model creates a software perimeter to dynamically control user and device accesses based on the assets they are trying to access.
-
02 Endpoint secu

Endpoint security solution detects suspicious user behavior for rapid response. Specifically, it monitors communications between and the status of computers and servers and alerts administrators if abnormal or suspicious behavior is detected. Administrators can analyze the logs of computer status, communications, and other information provided by Endpoint Detection and Response (EDR) to take action.
-
03 User authentication

This service provides ID authentication, ID password management, single sign-on (SSO), and access control via the cloud.
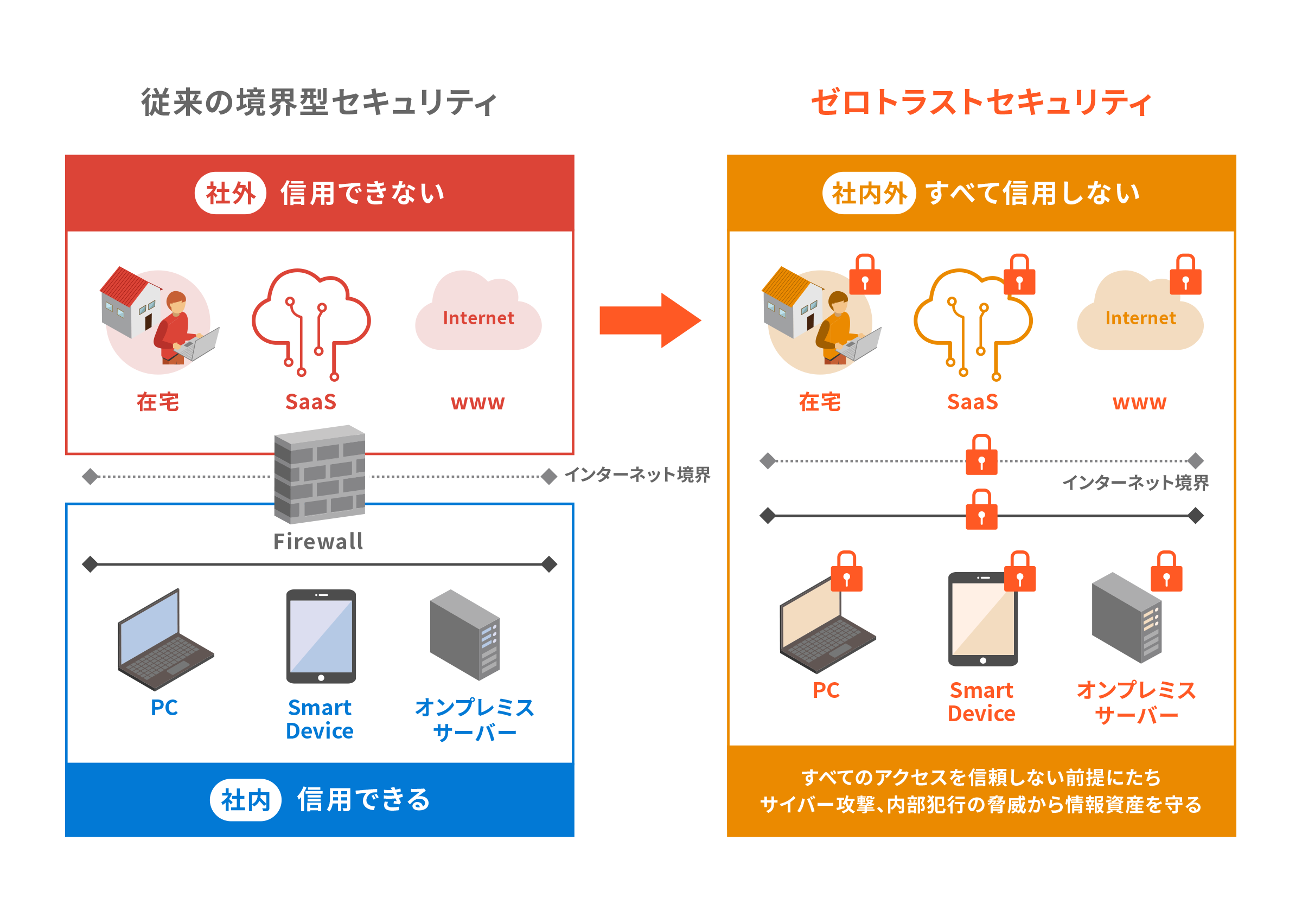
Difference from traditional security
Traditional perimeter-based security uses firewalls to protect the perimeter between internal and external networks based on the premise that malicious actors are outside, not inside. However, this model is vulnerable to latent threats that have infiltrated your network. Some threats can also easily cross the perimeter. Zero-trust security, on the other hand, regards identity as the perimeter to protect, assuming that every access must be validated, regardless of where it originates, internally or externally.

Why zero-trust security?
Traditional on-premise systems typically store information assets in an internal network that can only be accessed from an external environment through a VPN. As a result, they have used a perimeter-based security model to build firewalls between internal and external networks to prevent unauthorized access and data breaches.
However, the perimeter model is no longer sufficient as organizations move to cloud models. Using SaaS, PaaS, IaaS, and other cloud services means that some of their assets are exposed to the outside world, requiring a new security approach to maintain defenses against unknown attack vectors that arise daily. Zero-trust security has emerged for this purpose.

Use scenarios
Various scenarios require security measures.The following are some of them.





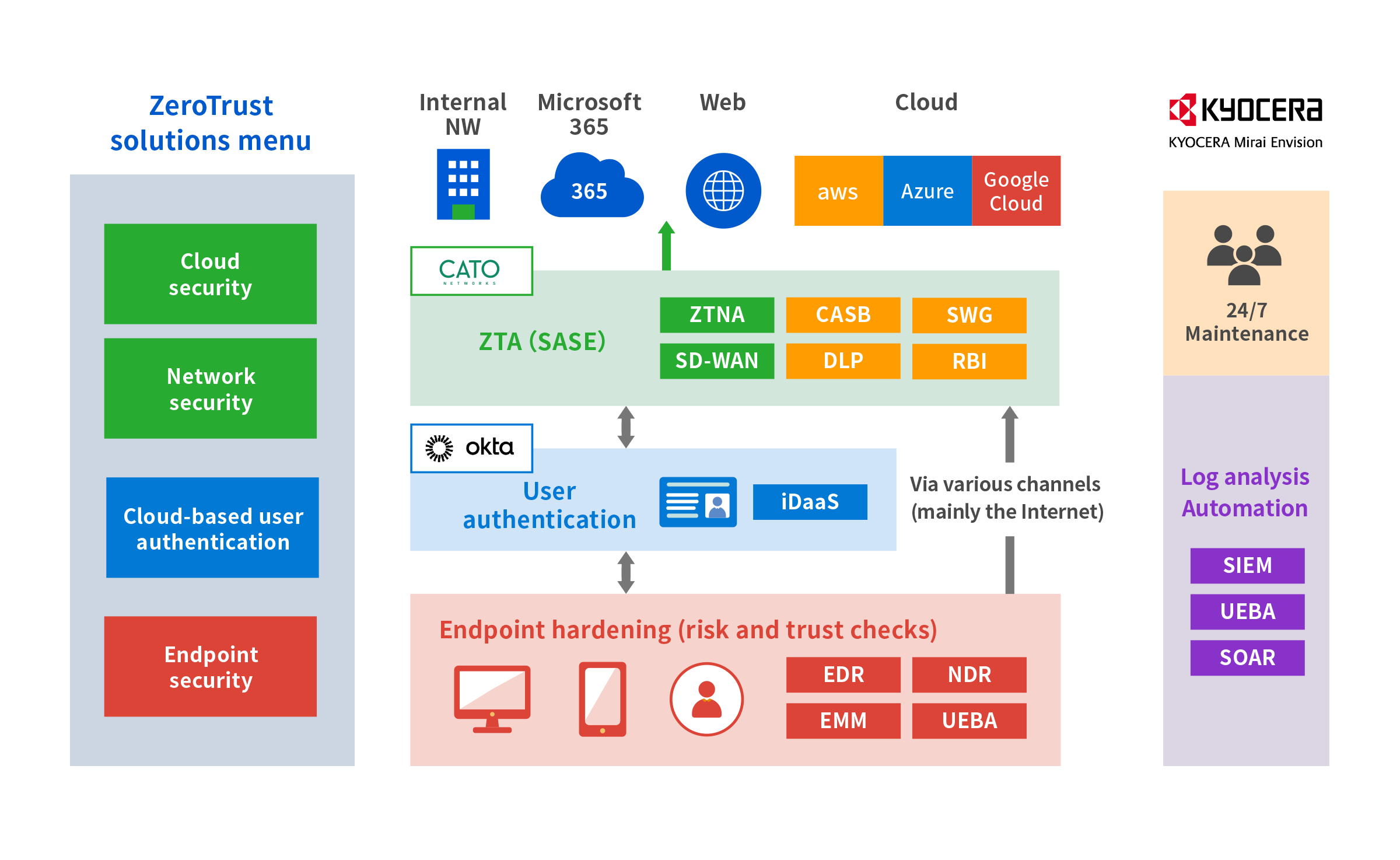
KCME's zero trust security solution
Our total security solution helps organizations shift to zero trust with comprehensive coverage of zero trust access, endpoint hardening, user authentication, log analysis, and automation. We also provide 24-7 maintenance so you can leave the post-implementation operations to us.
Features
-

Cloud and network security
The solution uses Cato Cloud to provide various cloud and network security capabilities as a single service, including ZTNA, SD-WAN, CASB, DLP, SWG, and RBI.
-

Cloud-based user authentication
Achieve unified user authentication, single sign-on, and privilege control.
-

Endpoint security
We will select and deploy endpoint security tools that suit your environment. This provides multi-layered endpoint protection that consists of three shields, using advanced protection, detection, investigation, response, and human eyes.
-

One-stop service from proposal to implementation to operation
KCME offers a one-stop service, including consulting, PoC, proposal, implementation, and operation.
-

SOC(Security Operation Center)
We have a 24-7 SOC. You can also rely on us for operations, including monitoring events, responding to incidents, changing settings, and reporting for you.
- Zero Trust Security
- Cato Cloud
Contact Us
We will contact you within 1-2 business days.
Please feel free to contact us.

