Enterprise
solutions
We provide services and solutions in communication infrastructure, DX, cloud, and security for enterprises, educational institutions, hospitals, factories, nursing homes, and other customers.

- Home
- Businesses
- Enterprise Solutions
KCME and its partner ecosystem across Japan deliver telecom infrastructure, digital transformation, security, and related solutions for enterprises in different business situations.
Our mission is to address challenges in seven fields of social infrastructure: telecommunications, safety, medical and nursing care, education, transportation and logistics, population decline, and regional economies. In pursuing this, we offer digital transformation, platform, cloud, communications network, application, and security tools that help many businesses address their challenges in these fields.
Our offerings cover all phases of proposal, implementation, and support.
Telecom infrastructure
We build local 5G, Wi-Fi 6, and other network environments, providing 24/7 maintenance and network-based solutions.

Local 5G solutions
A local 5G nTelecom infrastructureetwork is exclusively for you, based on your private radio station in the premise, unlike wide area 5G networks provided by operators. We offer deployment support services.

Wi-fi 6 solutions
We provide a Wi-Fi service that ideally suits your environment covering the entire process from requirements analysis, vendor selection, equipment selection, to system operations and maintenance. The total service is based on our technological abilities and expertise accumulated since the days of analog communications.

sXGP
SXGP (shared Extended Global Platform) is a private communication method using 4G/LTE, a standard communications technology that smartphones and other devices use. Private LTE will provide superior mobility and higher voice quality than Wi-Fi. SXGP is also available as a replacement for PHS (Personal Handy-phone System), which is still in use but was introduced many years ago.
MF SmartPole
Customers can select items to install on this multi-functional pole, including public wireless equipment, sensors, cameras, streetlights, and signage. Sustainable use cases that contribute to the future IoT and mobility infrastructure are expected.

Enterprise networking
Multi-vendor, one-stop solution for enterprise infrastructure construction

Telecom construction
We construct communication infrastructure for vendors, facility providers, subcontractors, local governments, and other organizations.

GPON
If you have large premises, many floors, or a good many users, this is a cost reduction opportunity for you.
GPON (Gigabyte Passive Optical Networks) is a faster, highly maintainable optical network infrastructure that saves more costs when deployed at scale.

Core networking
We support core network verification, construction, maintenance and operations. Since the Internet became common, these networks have been at the core of the Internet and mobile networks.

Wireless network optimization
Optimization based on a wireless site survey is essential to build a stable wireless network.
We provide optimization services for wireless LANs in companies and facilities, public Wi-Fi networks, and even the latest 5G networks, taking advantage of our expertise accumulated for many years through projects for mobile carriers in and out of Japan.

24/7 Maintenance
We monitor your equipment, detect failures and respond to them 24-7. We also offer custom plans for you such as on-site, remote, and limited-hours support.
DX
(Digital Transformation)
We help you achieve your digital transformation with solutions using IoT, AI, and big data.
IoT
We build and provide an IoT platform that connects things in the field with the management.
We can provide a wide range of IoT solutions, including communication devices (hardware), IoT infrastructure, and analysis and visualization solutions.
LPWA Communication Module
The module, embedded in devices, enables power-saving and long-distance LPWA communication.
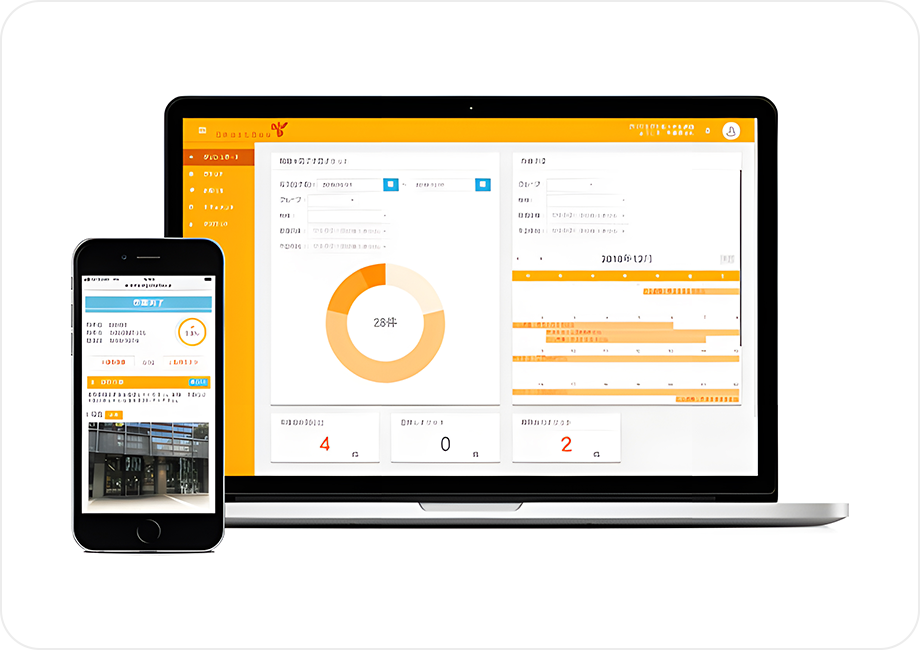
SmartBee
SmartBee cloud service enables centralized management of work items and on-site information, reducing management workloads. Furthermore, it will allow managers to understand the situation at the inspection site in real time, leading to less mistakes and lower costs.

Solutions for logistics
These solutions accelerate digital transformation in logistics by visualizing assets for more efficient delivery management.
AI/big data
With our tools, we accelerate your digital transformation of individual or an entire business processes. We also offer support after implementation.
Alteryx
Alteryx is the definitive self-service data analysis tool.
It offers high-speed processing without programming from pre-processing data from multiple sources to analysis using machine learning to data output.

UiPath
With a user-friendly interface and recording feature, the UiPath RPA solution allows users to easily automate repetitive human operations on a computer for routine tasks. The automation is expected to shorten work hours and improve quality, as well as give employees an opportunity to consider how to improve their work efficiency.
Other solutions
We develop and provide solutions that combine the latest ICT and communication technologies to solve our customers' problems.

Wonder Cloud Works
Wonder Cloud Works cloud service integrates WowTalk business chat from a Japanese vendor, WPS Cloud Pro cloud office, and CAMCARD BUSINESS cloud address book. Using a single ID and password, you can access all the tools. Just simple.
Security
We provide a safe and secure security infrastructure that responds quickly and flexibly to changes in business models or digital transformation and other platforms. It is an essential building block for a foundation that supports business enhancement.

Zero Trust security
The traditional security approach is about boundaries based on the idea that an internal network is safe and the outside is not. Instead, the Zero Trust approach assumes that every access to data has a security risk and requires authentication for each access to ensure the data security.
In other words, the approach checks these for every access to an internal network: whether the device is infected with a virus, whether the accessing device is registered in the organization's system, etc.